I recently started practicing challenges on the picoCTF website. One of the challenges is to obtain a flag from a program. And the program despite its .exe name was ELF binary. Ok, so few initial steps:
1) Can I run it? -> no, it complains about some dependencies
There were some missing libgnat-7 dependencies. Hmm, how to install them? Docker containers come in handy. Especially that a binary while viewed in hex, had a Ubuntu 18 string. Thus I used Ubuntu-18 container and installed libgnat-7.
2) Can I run it now? -> Yes, but it hangs
Why does it hang?
Let’s install GDB in our docker container and run it with gdb and use the below steps:
root@37a6e515eafa:/workspace# gdb svchost-patched1
GNU gdb (Ubuntu 8.1.1-0ubuntu1) 8.1.1
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from svchost-patched1...(no debugging symbols found)...done.
(gdb) c
The program is not being run.
(gdb) run
Starting program: /workspace/svchost-patched1
warning: Error disabling address space randomization: Operation not permitted
^C
Program received signal SIGINT, Interrupt.
0x00007f7e9ba4d654 in __GI___nanosleep (requested_time=0x7ffc66294bb0, remaining=0x7ffc66294bc0) at ../sysdeps/unix/sysv/linux/nanosleep.c:28
28 ../sysdeps/unix/sysv/linux/nanosleep.c: No such file or directory.There is some kind of call to nanosleep() function there. Maybe we can somehow make it sleep for a shorter period? Or even zero? How would I patch that?
With a little bit of Googling, I found this tool: https://ghidra-sre.org/ Which can show disassembled versions of a binary and much much more. Browsing through different functions I discovered this:
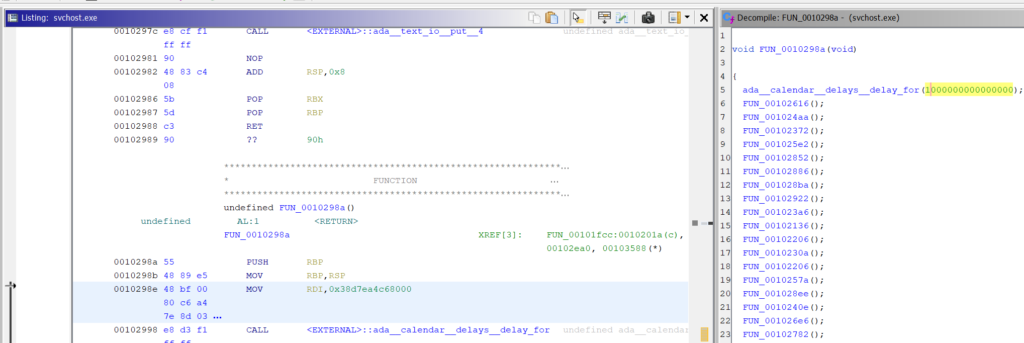
And fortunately, Ghidara can simply replace the value with an arbitrary value by right click -> Patch Instruction (or Ctrl_+ Shift + G)
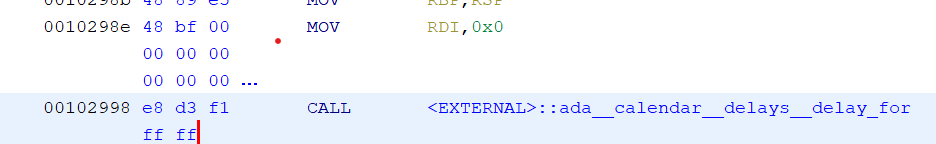
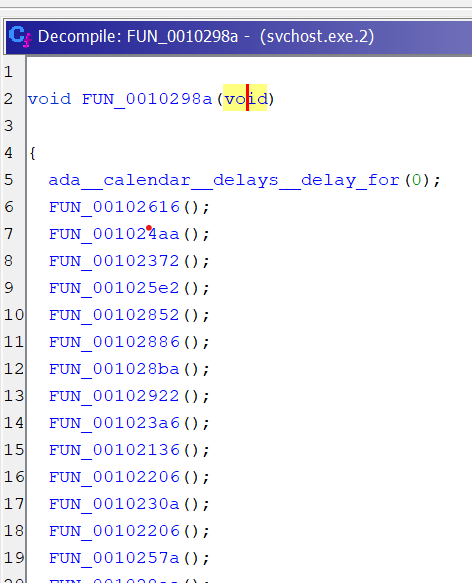
Now, what’s left is to export the modified version of a program with “O” (or File -> Export Program) and run it in the docker container.
And, as expected, the wait is no longer there