Let’s imagine we have an internal web app and we want to expose it securely over the internet only to a selected group of people. There are multiple ways to do it. One that is often used is to set up the virtual private network (VPN). In my home lab, I use VPN a lot. But with VPN it’s easy to expose too much. And what if I want to share an app just for development purposes with someone else. And also, I want the process to be as simple and straightforward as possible. It should be a solved problem in 2021, right? Well, it’s kind of is with Teleport. I use it a lot in my home lab because it saves me a lot of time and still keeps my containers/access organized and secure. Let’s go through concrete examples of exposing Jenkins and home router.
Short version
Assuming you have the Teleport already set up, you can add your apps in a similar way to described below:
1. In the teleport.yaml add:
- name: "jenkins"
uri: "https://jenkins.jarosik.vpn"
insecure_skip_verify: true
rewrite:
redirect:
- "olobok-proxy"
- "jenkins.jarosik.vpn"
- name: "router-olobok"
uri: "http://192.168.100.1:80"
rewrite:
redirect:
- "olobok-proxy"
- "192.168.100.1"2. Setup wildcard SSL certificates (very first time only)
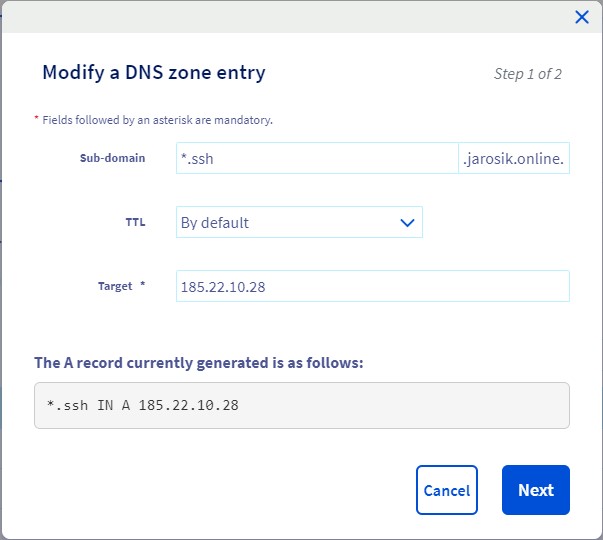
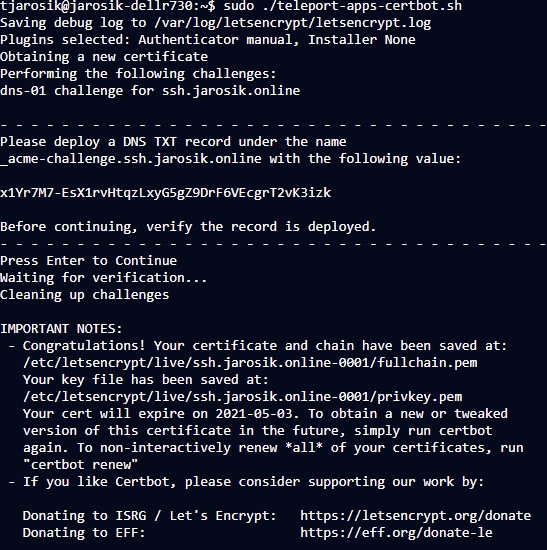
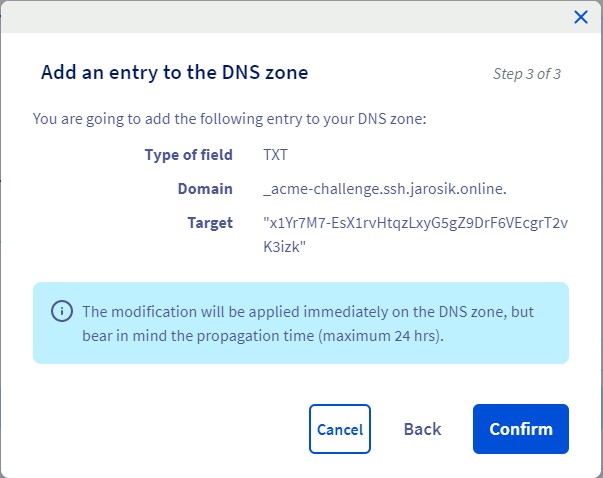
3. Go to “Applications” in your Teleport and you should be able to access 2 apps:
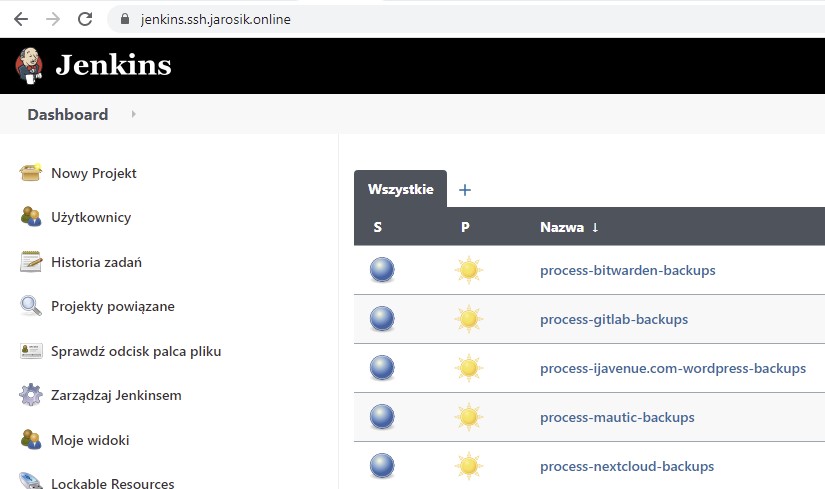
and also to “https://router-olobok.ssh.jarosik.online”
Long version
The “short version” is lacking details, so let’s add them here. You can find documentation about the Teleport here: https://goteleport.com/teleport/docs/ and the application section here: https://goteleport.com/teleport/docs/application-access/ It might seem like a lot, but most of these settings are very first time only. One detail that I initially missed is that for Jenkins I needed to add a rewrite for redirections to work correctly. Also, I keep teleport behind HAproxy which serves multiple domains already, so I needed to slightly modify the config to allow multiple subdomains just for the teleport.
acl teleport-acl ssl_fc_sni -i ssh.jarosik.online
acl teleport-apps-acl ssl_fc_sni -m end .ssh.jarosik.online
use_backend teleport-web-https-backend if teleport-acl
use_backend teleport-web-https-backend if teleport-apps-aclAnother interesting thing is that you can register an app from anywhere. This is an example of a web app running in a Virtualbox VM on my laptop and connected with a reverse tunnel to the teleport. All you have to do is this one line:
sudo teleport start --roles=app --token=$APP_TOKEN --auth-server=ssh.jarosik.online:443 --app-name="inout-app" --app-uri="http://localhost:8080"For the above line to work, you have to have the teleport proxy exposed to the internet. But it’s a similar process if you want to expose an ad-hoc SSH node, e.g. your Rasperry Pi. And you only need to set up this teleport proxy once. After that, you can expose any app with just a single line. The “inout-app” will be exposed as “https://inout-app.ssh.jarosik.online” WITHOUT any additional configurations and with correct TLS/SSL certs (so a web browser won’t complain). And it will also appear in the teleport applications list like any other app. This “one-liner” kind of expose won’t work well because redirections will redirect to real sites. But it might be still useful in some cases. The config version works well, and I exposed many apps that I need (including a central logging system, routers UI, or PowerDNS). And because it’s over https, you can just open a web browser on your smartphone and have full access without any additional configuration!